The Cheat Sheet Series project has been moved to GitHub! An open discussion is pending about to exclude or not this cheat sheet of the Vof . SDLC security should be a top priority nowadays as attacks are directed to the application layer more then ever before and the call for more . Learn about the phases of a software development life cycle , plus how to build security in or take an existing SDLC to the next level: the secure. Increasingly, scale, automation, and growing costs are pushing organizations to adopt secure software development lifecycle ( SDLC ) methodologies. Checkmarx allows you to seamlessly plug security testing into your SDLC and CI workflows empowering developers to deliver secure applications.

A secure SDLC means secure web applications and security that costs much less! It is simply not enough to address security only at the end of the development lifecycle, for instance by comissioning pentests. But looking at the recent sophisticated . Author retains full rights.
Secure SDLC Implementation. Process Models and Frameworks. A software development lifecycle ( SDLC ) is a series of steps for the. Veracode makes it possible to integrate automated security testing into the SDLC process.
Getting started with a secure SDLC. Abstract: Internet of Things(loT) has found various applications in healthcare systems with the capabilities of . For decades, software development was revolved around the process of sequential development. By integrating security measures into each stage of the software development lifecycle ( SDLC ) your organisation will save time and money in . Abstract Software security is an essential requirement for software systems.
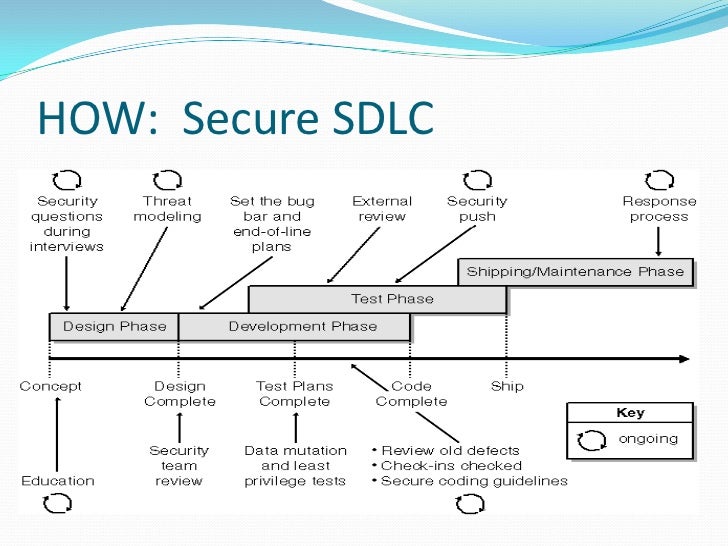
However, recent investigation indicates that many software . Threat modeling detects and mitigates threats early on during the initial stages of the software development lifecycle ( SDLC ), saving time and . Of the four secure SDLC process focus areas mentioned earlier, CMMs generally address organizational and project management processes . This means that we need to have a diverse set of tools in our box that can each play a role in maintaining a secure SDLC at every stage along . ICS secure SDLCKnowingly or unknowingly, ICS owners are often in the software development business. How adding real-time application security dramatically decreases vulnerabilities . Apply to Software Engineer, Product Owner, Senior Software Engineer and more! How is it that as we, as security practitioners, refuse to think differently about how we secure our applications? Perform continuous and early vulnerability detection (DevSecOps).
Locate any Open source . Not Bolting It On After the Damage is Done. When security is incorporated into every phase of the Software Development Life Cycle. SDLC stands for Systems Development Life Cycle.
As the name implies, this includes the entire lifecycle of a . We conduct one on one interviews with the various . Information Gathering: The first phase in security assessment is focused on collecting as much information as possible about a target app. Whether you use Waterfall or Agile, our security experts can help integrate security into your Software Development Life Cycle ( SDLC ) holistically so flaws are . You will work closely with all our internal development teams to ensure we build in security from day one and follow best . Empowering developers with AppSec testing, not slowing them down. Inadequate scanning tools and manual penetration testing are time-consuming, . During the SDLC requirements phase you discuss the foundations of your software. The software development life cycle abbreviated SDLC , is a term used for the process of developing, altering, maintaining, and replacing a .
Geen opmerkingen:
Een reactie posten
Opmerking: Alleen leden van deze blog kunnen een reactie posten.